Some time during freshman year of College, a thousand flyers blanketed campus. This was nothing new, as students have been hanging flyers since the beginning of time. Flyers are supposed to have a literal stamp of approval from the college in order to be hung, though that policy is supposedly selectively applied, and is only used as an excuse for the college to take down flyers they don't like... alledgedly. But sometimes, even if the college wants to take down the flyers, there are just too many.
During my freshman year, one such wave of flyers were posted around campus. Each one had a purple icon with a white outline of an insect, along with the words "What's Fizzin'?"
Dumbest tagline I have ever seen. But there were just so many flyers that I had to see what it was all about. Scanning the QR code and downloading the app showed that it was some college-focused anonymous social media platform. But how secure was it really?
I set up my phone to use HTTP Toolkit and opened the app. Network connection failed? Wha?
Certificate Pinning is a pain in the ass. Back in my freshman year, I gave up there. Today, I gave it another shot. Turns out, the pinned certificates are contained inside the Info.plist!
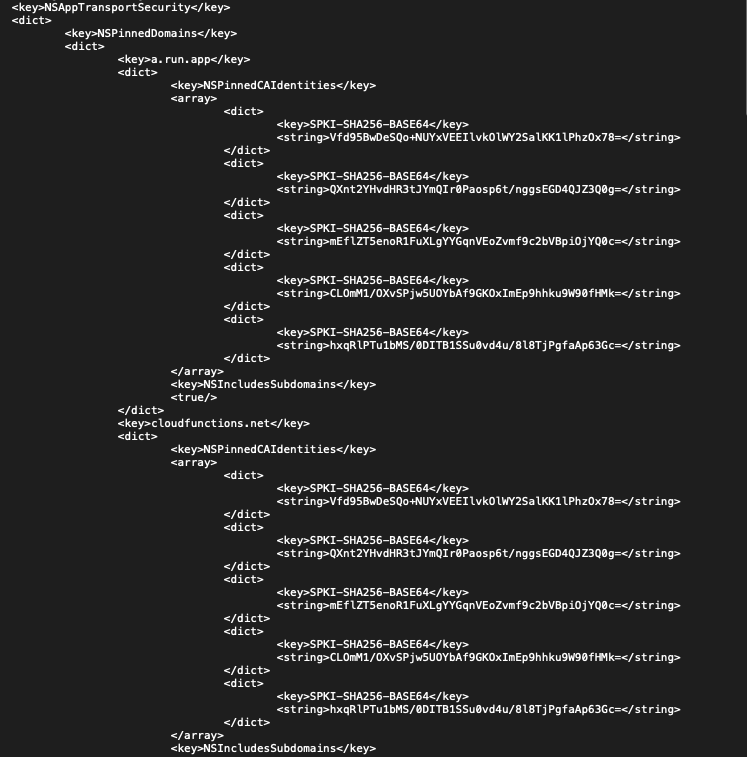
But what if... I were to insert my HTTP certificate and disguise it as one of their own certificates? [chuckles] Delightfully devilish, Seymour.

All I had to do was generate the SPKI-SHA256-BASE64 for my certificate. Apple makes this incredibly easy. Just use this command...
cat ca.pem |
openssl x509 -inform pem -noout -outform pem -pubkey |
openssl pkey -pubin -inform pem -outform der |
openssl dgst -sha256 -binary |
openssl enc -base64...to make it. It takes .pem as well as .crt files, so HTTP Toolkit certs don't need any kind of conversion. After that, all I had to do was get my iPhone to trust the certificate. Pretty easy AirDrop, thanks to Handoff. (Double check that you have it enabled after installation in Settings > General > About > Certificate Trust Settings)
God bless Filza. One Info.plist edit later, and I had successfully inserted it... and it worked!
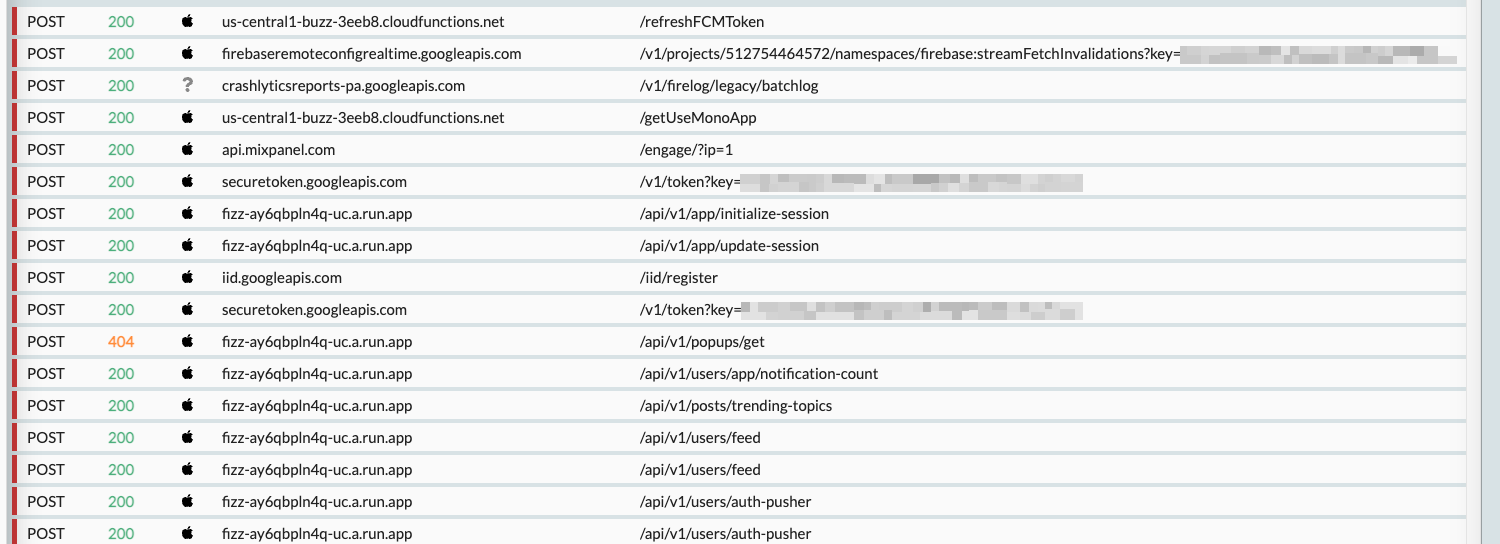
The data collection is... not nothing... but certainly not the worst I've seen.
But do you really need to know that I use Verizon?
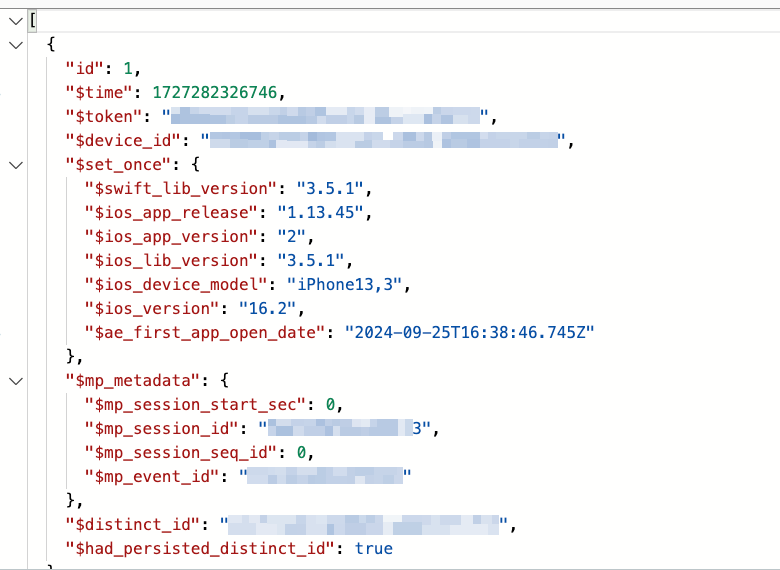

Includes cumulative app view-time, so that's fun 🙃
This MITM setup came in not-handy when a controversial video was anonymously posted to the platform earlier this month. I wanted to download this video, as one does. While the app has a native feature to download posted images to your device's camera roll, it does not have a similar function for videos. My MITM setup from earlier in the month came in handy to grab the request.
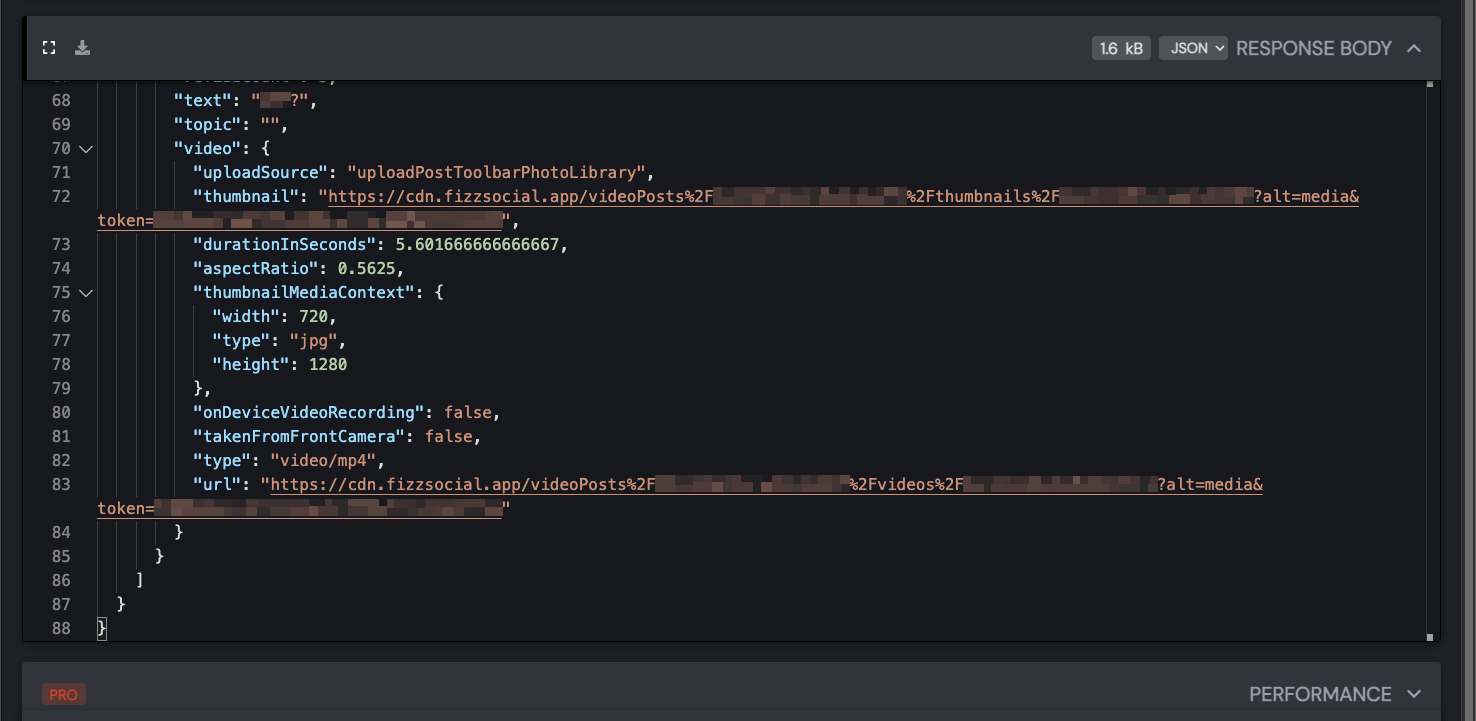
I was able to use the URL to download the highest-quality-possible version of the video, instead of using a shitty screen recording, or even worse, taking a video of the phone screen (which I saw someone else do). I checked for EXIF data, but they've anonymized it. So turns out it's pretty secure, which I'm happy about, though they really should add a native way to download videos. The app is complete brainrot, though, so 3/10.
